By-passes
What are by-passes?
By-passes are defined in computer science as methods to access a protected resource without authorization. Bypass techniques are also used as a lockpicking technique and its definition remains very similar.
Indeed, bypass techniques are found everywhere on all types of systems. These tricks consist in exploiting at best one or more flaws present on a security and thus manage to open it, regardless of its supposed level of security.
How about lockpicking?
To make an easily understandable analogy, if we had to pick the lock of a door to enter a house, the bypass would be to go through a window. All the magic of this method is to find “the window”.
Sometimes it’s very simple, so simple that you manage to open faster than if you had the key! But sometimes it’s more complicated too…
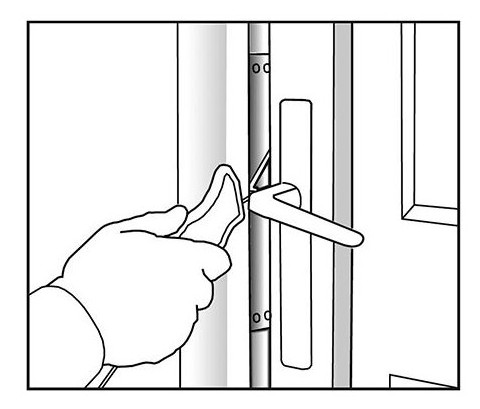
This article gives you an overview of some common bypass processes. In this video you can see that it is enough to leave only the two sizes of the bottom of the key. Doing so, we free ourselves from the trims so as to open for sure:
Here it is the blocking pawn of the handle that will be lowered. We use of a pointed needle from the bottom of the rotor. This will cause the opening:
In this video it is a small metal shaft that will allow us to trigger the web, without touching the cylinder:
Yet another way to bypass some padlocks:
You can see that there are many ways to bypass a security device. It’s up to you to study the systems and find the flaws…
And of course come to the ACF to share them with us!
Thanks to Bertrand, William and Fabien for the videos




